beemNet
beemNet is a private network that protects all connected devices and networks from internet-based cyber threats, while also enhancing privacy through targeted anonymization and encryption.
Customers can choose from four Security Editions, each tailored to different protection needs within the beem Hub:
Each Security Edition builds upon the previous one, with higher tiers including all features of the lower ones.
The Essential and Standard Security Editions are designed as highly standardized “Activation-Business” offerings. Starting with the Standard Security Edition, a dedicated tenant is provisioned, enabling seamless upgrades to higher Security Editions.
Access to beemNet
Access to the beemNet is enabled through user and site licenses. site licenses are beemNet options that are combined with the site connection, thereby integrating it into the beemNet. User licenses with a mobile subscription are integrated into the service by activating a beemNet option offered by Swisscom for the respective connection and by linking the connection with a user identity. This makes the associated functionalities available to the authenticated user.
Users who do not have a mobile connection, or whose mobile connection cannot be combined with the service, can be integrated into the service with a user license without a mobile subscription ("Protect License") offered separately by Swisscom.
Infrastructure
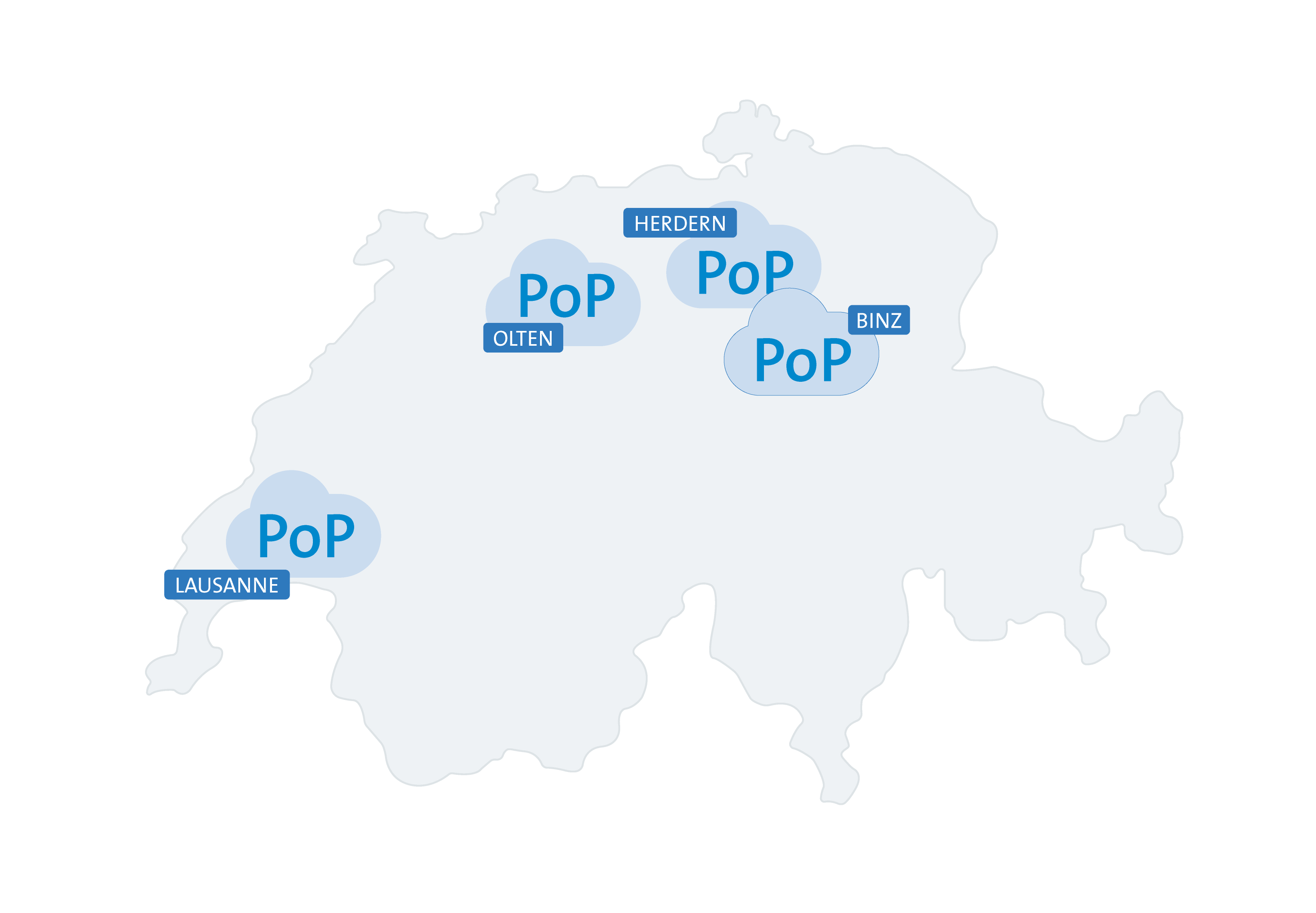
Swisscom operates four geographically redundant Points of Presence (PoPs) within Switzerland, with built-in automatic failover mechanisms to ensure continuous service availability across all sites.
Firewall as a Service (FWaaS) & Secure Web Gateway (SWG)
FWaaS offers the ability to identify applications through various characteristics, such as Layer-7 Deep Packet Inspection (DPI), URL, protocol and port numbers, destination IP addresses, and more. This is used in combination with comprehensive, rule-based control. The DNS proxy secures DNS entries through information from authoritative DNS servers and DNS reputation feeds to block access to untrusted or malicious websites. URL and IP reputation, categorization, and filtering enable safe browsing and block harmful websites. The TLS/SSL proxy opens and inspects encrypted traffic to detect threats and prevent data leaks. IPS detects and prevents vulnerabilities based on signatures and anomalies. By updating vulnerability signatures and anomaly detection in real-time, continuous protection is ensured.
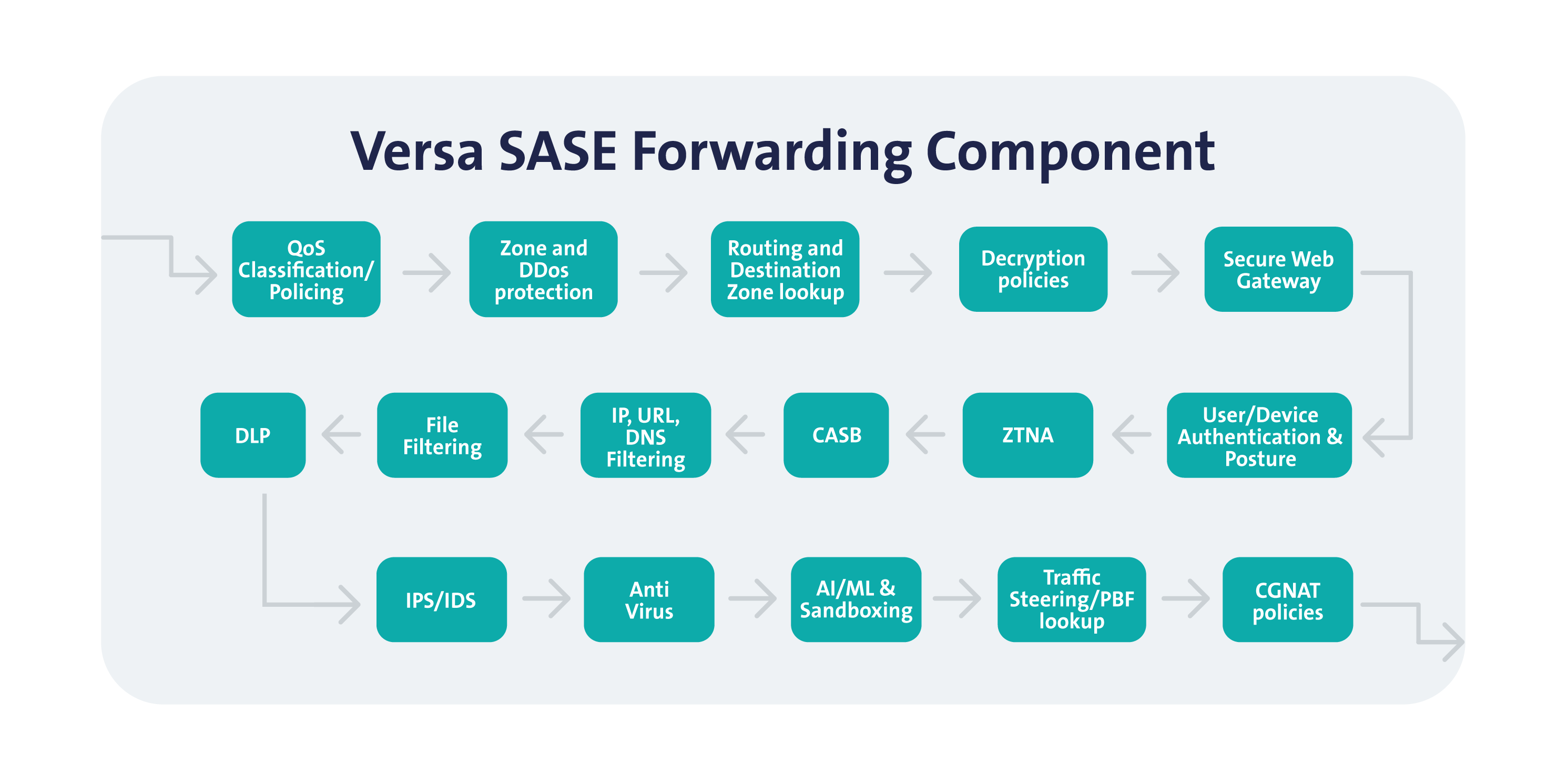
Figure: Versa SASE Forwarding Component illustrating the layered security and traffic processing pipeline within beemNet’s infrastructure.
Efficient management, protection, and monitoring form the foundations of secure web access control. Predefined policies and bandwidth prioritization optimize web traffic. Threat defense provides comprehensive protection against malicious websites and enables a quick response to new attack patterns. Real-time prevention of data leaks secures unauthorized data transmissions and ensures compliance with regulations. Security for mobile employees enables protected web access from any site and device. Real-time monitoring ensures seamless control and blocking of inappropriate content to guarantee secure and managed web access. Together, these components form a holistic security solution for secure and managed web access:
- Statefull Firewall
- Application Visibility
- Next-Generation Firewall
- IP-Filtering
FWAAS application identification capability identifies all applications with features such as Layer 7 Deep Packet Inspection (DPI), URL, protocol and port numbers, destination IP addresses and more, combined with comprehensive policy-based control.
Stateful Packet Inspection (SPI)
Stateful Packet Inspection (SPI) is a core security capability integrated into our SASE platform to provide intelligent, context-aware firewall protection for all internet-bound traffic. Unlike stateless filtering, which only evaluates individual packets, SPI tracks the entire state and context of network sessions, enabling the platform to make informed decisions about traffic legitimacy. In our solution, SPI is enforced through Internet Protection Rules, which are applied per tenant and dynamically evaluate traffic based on a combination of match criteria (e.g., applications, users, geolocation, IP addresses, and protocols) and predefined security enforcement actions (e.g., allow, deny, or profile-based inspection). SPI ensures that traffic is evaluated not only by source and destination but also based on behavioral patterns and protocol compliance. For example, it can recognize and validate the proper sequence of a TCP handshake or detect deviations from normal session behavior, rejecting suspicious or malformed connections automatically. The inspection logic is embedded into the firewall enforcement engine and works in concert with:
- Application & URL filtering
- IPS (Intrusion Prevention System)
- Deep Packet Inspection (DPI)
- TLS/SSL decryption
- IP reputation and DNS security
- Role- and identity-based access policies
This layered approach allows SPI to be highly effective at detecting session hijacking, protocol abuse, and spoofed connections while maintaining performance through optimized processing at the point of presence (PoP). As part of the beemNet architecture, SPI plays a key role in delivering secure and policy-compliant internet access for both fixed and mobile users, aligned with Swisscom's security tiers.
Deep Packet Inspection (DPI)
Deep Packet Inspection (DPI) is a key inspection technique used in our SASE-based beemNet infrastructure. It analyzes the full payload of data packets, not just header information, to detect and control complex traffic patterns and threats in real time. DPI enables advanced visibility and filtering by examining the content of internet traffic, allowing for enforcement based on:
- Protocol compliance and anomalies
- Application signatures and behaviors
- Embedded malware, spyware, or other threats
- Potential data leaks (DLP)
- Policy violations and inappropriate content
In our solution, DPI is primarily activated from the Security Level 2 upward. At this stage, the traffic, including encrypted connections, is decrypted by the TLS/SSL proxy and inspected inline. DPI works in conjunction with:
- Stateful Packet Inspection (SPI)
- URL and IP Filtering
- Antivirus and Antimalware Engines
- Intrusion Detection and Prevention Systems (IDS/IPS)
DPI is essential for detecting advanced threats that bypass traditional firewalls and enables the application of granular security controls. Its effectiveness relies on continuous updates to protocol recognition, threat signatures, and behavioral heuristics. As part of the beemNet security stack, DPI contributes significantly to the ability to block malicious content, enforce usage policies, and ensure regulatory compliance—all while maintaining a seamless user experience.
DNS Proxy & Security
DNS Proxy & Security is a comprehensive solution designed to protect networks and clients at the DNS layer by combining advanced filtering, threat intelligence, and traffic management capabilities. It includes the following core components: DNS Forwarder, DNS Split Proxy, DNS Proxy, DNS Threat Feeds, and DNS Firewall.
- The DNS proxy plays a central role in securing DNS traffic. It leverages information from authoritative DNS servers and continuously updated DNS Reputation Feeds to block access to untrusted, unknown, or malicious domains, including those associated with Command & Control (C&C) infrastructures used by attackers. It also improves DNS resolution speed and simplifies DNS management.
- DNS Security & Filtering protects against a wide range of DNS-based threats, including DNS hijacking, reflection and amplification attacks, phishing, malware, ransomware, and botnets. This protection is enforced directly at the DNS layer, preventing threats before they reach the network or endpoints.
- The DNS forwarder is used when a DNS server cannot resolve a query using its local DNS tables and must forward the request to an external resolver.
- The DNS Split Proxy enhances efficiency by separating internal (e.g., within a corporate domain) and external DNS queries, ensuring optimal routing and resolution performance.
- DNS threat feeds are dynamic, global datasets that provide real-time intelligence on malicious domains. These feeds are continuously updated using data from hundreds of sensors worldwide, enabling proactive blocking of newly registered or suspicious domains until their reputation is verified.
- The DNS Firewall inspects every DNS query and blocks access to domains identified as dangerous, such as phishing sites or compromised web servers, thereby adding another layer of security. Together, these components form a robust DNS security architecture that not only accelerates domain resolution but also significantly reduces the attack surface by preventing access to harmful domains at the earliest possible stage.
URL & IP-Reputation
beem NGFW provides a rich set of URL and IP categorization and filtering capabilities in 80+ URL categories to enable safe browsing while blocking malicious sites. The URLs are categorized by reputation, risk, and trustworthiness. In addition to predefined classes, beem provides support for user-defined/custom classes that can be created and managed as needed. Hundreds of millions of domains and 13+ billion URLs are scored and classified for maximum threat coverage.
86 predefined URL categories including generative AI and general Internet, to improve employee productivity; inappropriate sites like gambling or pornography to avoid legal liability; and bandwidth management including voice and video sites.
- The URL database is updated periodically via security package updates without the need for VOS or software upgrades.
- Real time cloud lookups of URL categories for those uncategorized in the VOS cache
- Custom URL categories based on Regex and/or Fixed String Match
- Customizable captive portal screens for policy enforcement and redirection
- Support for Block, Inform, Ask, Justify, Override, and Authenticate Pages
TLS & SSL Proxy & Decryption
- Protects against threats hidden in encrypted traffic by breaking open and inspecting TLS/SSL traffic and applying additional security policies for threat and data protection.
- Directs encrypted traffic based on application signatures, scans encrypted content for malware and exploit prevention, and detects and prevents data leakage to enforce company compliance.
- Support for transparent or split-proxy modes.
- Supports TLS versions 1.0, 1.1, 1.2, and 1.3 and has been ahead of many security vendors in support for TLS v1.3. Recommendation to use TLS 1.3 with TLS Proxy: beem recommends the use of TLS 1.3 for higher security as it incorporates improvements to ensure the confidentiality and integrity of communications.
- Perfect Forward Secrecy (PFS) employs the use of ephemeral keys to overcome confidentiality concerns. PFS is mandatory with TLS 1.3. By generating a unique session key for every session that a user initiates, even the compromise of a single session key will not affect any data other than that exchanged in the specific session protected by that particular key.
- Parts of the handshake (server certificate values such as CName and SAN) are encrypted. This prevents malicious third parties (that rely on examining server certificates) from eavesdropping on the connection.
Intrusion Detection System (IDS)
An Intrusion Detection System (IDS) is a passive monitoring component used to analyze network traffic and identify suspicious or unauthorized activity. It operates out-of-band, meaning it receives a mirrored copy of the traffic rather than being inline with the flow. The IDS inspects the traffic using:
- Signature-based detection: Compares traffic patterns against a regularly updated database of known threat signatures.
- Anomaly-based detection: Identifies deviations from established traffic baselines to detect novel or zero-day attacks. Administrators can define vulnerability profiles that specify detection rules, thresholds, and response actions (e.g., alerting or logging).
These profiles can be: - Predefined, covering typical use cases like client protection, malware detection, or OS-specific threats.
- Customized, where rules are adapted to organizational needs (e.g., filtered by CVSS score, operating system, or traffic direction). The IDS logs detected events, and optionally captures packet data for further analysis. These logs and captures are typically forwarded to a centralized analytics system for visibility and correlation. By placing IDS at internal junctions (e.g., between VLANs or critical systems), organizations gain deep visibility into east-west traffic, helping to detect lateral movement or insider threats.
Intrusion Prevention System (IPS)
An Intrusion Prevention System (IPS) is an inline security mechanism that not only detects malicious activity but actively blocks it. Unlike IDS, the IPS sits directly in the traffic path and can drop or reject packets in real time. All traffic passes through the IPS before being forwarded, allowing immediate response to detected threats. Detection methods include:
- Signature-based detection: Matches incoming traffic against a curated database of known attack signatures.
- Anomaly-based detection: Compares real-time traffic behavior against established baselines to detect unusual activity. Actions that can be enforced by the IPS include:
- Dropping malicious packets or entire sessions
- Resetting connections from client or server side
- Logging events with optional packet capture
- Generating alerts for security teams The system uses vulnerability profiles—collections of detection rules categorized by criteria such as:
- CVSS score range
- Operating system or application
- Attack vector or protocol
- Rule type (signature or anomaly) Profiles can be predefined or custom-built using a rule editor that allows filtering by threat ID, severity, or detection confidence. Additionally, administrators can upload their own custom rules in standard formats (e.g., Snort-compatible), which are compiled and applied to traffic. To avoid service disruption, the system supports asynchronous rule compilation, meaning new rules can be prepared in the background while previous ones remain active. For fine-grained control, thresholds and exceptions can be configured—allowing, for instance, specific IP addresses to bypass certain rules, or limiting actions based on hit rates within defined time intervals. An IPS plays a critical role in preventing exploitation of vulnerabilities and ensuring that unauthorized traffic is intercepted before it reaches protected resources.
Malware & Antivirus Scanning
Malware protection is a core element of the beemNet security stack and is designed to detect and block malicious software before it can compromise endpoints or networks. This includes threats such as viruses, worms, Trojans, ransomware, spyware, and other unwanted code that may attempt to exfiltrate data or disrupt services. To ensure robust protection, beemNet integrates malware detection directly into its traffic inspection pipeline. This inspection is performed in real time and applies to both web and mail protocols, supporting:
- Multi-protocol inspection: Scans traffic over commonly used protocols including HTTP, FTP, SMTP, POP3, IMAP, and MAPI.
- Bidirectional analysis: Inspects both upload and download streams to identify malware attempting to enter or leave the network.
- File-type filtering: Filters based on file format, MIME type, or signature to prevent delivery of malicious content.
- Policy-based enforcement: Applies predefined or custom actions (e.g.,
Alert,Deny,Reject) in line with corporate security policies.
This capability is available from the Security Level 2 onward and plays a key role in protecting users across all connected networks.
Administrators can configure custom malware protection profiles, defining:
- The protocols and directions to scan (e.g., download only, or both directions).
- File types or categories to include in the scanning scope.
- Enforcement actions for detected threats:
Alert,Allow,Deny,Reject. Profiles can also include tagging and metadata for filtering, reporting, and policy assignment. Logs from malware detection can be forwarded to a centralized analytics platform for correlation and incident response. Malware protection is a foundational capability for preventing compromise, data leakage, and system disruption across all connected devices and services.
Antivirus (AV)
Antivirus (AV) scanning is a core function of network and endpoint security platforms, designed to detect and prevent known malware based on pattern recognition and behavioral analysis. It serves as a first line of defense against widespread threats like file-based viruses, Trojans, ransomware, and other malicious code. AV engines typically operate based on:
- Signature-based detection: Matching files and payloads against a database of known malware hashes and patterns.
- Heuristics and behavioral analysis: Identifying suspicious behaviors, such as self-replication, code injection, or abnormal file system access.
- Real-time updates: Continuously updated signature databases to address newly discovered threats. Antivirus scanning is integrated with:
- Web traffic inspection (HTTP, HTTPS)
- Email scanning (SMTP, POP3, IMAP, MAPI)
- File downloads and uploads
- Offline file scanning in cloud storage or via API-driven inspection Security policies can be configured to specify enforcement actions when malware is detected:
Allow(log only)Alert(raise notification)Deny(block delivery)Reject(actively drop connection)Recommended Action(based on risk score or policy presets) AV inspection is a vital layer in defense-in-depth strategies, especially when combined with sandboxing, reputation services, and anomaly detection systems. Properly tuned, AV scanning provides effective baseline protection with minimal impact on performance.
Application Layer Gateway (ALG)
The Application Layer Gateway (ALG) is a network function that facilitates the correct handling of application protocols requiring dynamic port assignments and embedded IP addressing, especially when traffic is subject to NAT (Network Address Translation) or firewall inspection. Certain protocols, such as FTP, SIP, PPTP, TFTP, and IKE ESP, establish secondary data sessions or include IP and port information in their payload. Without ALG, these sessions often fail when traversing NAT devices or strict firewalls, as dynamic connections are not correctly translated or allowed.
ALG operates by:
- Interpreting control traffic of specific application protocols
- Modifying embedded IP addresses and ports as needed for NAT traversal
- Dynamically creating temporary firewall rules (pinholes) to permit legitimate return traffic
- Maintaining session awareness to remove rules when sessions terminate
Example Use Case: FTP in Active Mode
In active FTP mode, two sessions are created:
- A control session (e.g., port 21) to manage commands like directory listing or file actions.
- A data session where the server initiates a connection back to the client to transfer files.
Without ALG, firewalls or NAT devices cannot recognize or permit the incoming data session, especially if the client resides behind a private IP address. ALG inspects the control channel, extracts the necessary IP/port information, rewrites it appropriately, and opens a pinhole in the firewall or NAT device to allow the session to succeed.
Access Network Integration
Integration with beem Office via the beemNet Option
The integration of beem Office with beemNet is achieved through a site-specific beemNet option. This enables all devices at that office site to be protected by the beemNet security perimeter. The beem Office router (e.g., Centro Business Router) establishes the connection to the beemNet PoPs, enabling secure, policy-enforced internet access for all connected devices.
Integration with Smart Business Connect (without BNS)
Smart Business Connect lines can be integrated into beemNet by activating a beemNet option for the respective connection. The integration currently supports only Smart Business Connect lines without the Business Network Solution (BNS) option. This limitation applies to the initial rollout phase of the beemNet integration.
Integration with NATEL® go via the beemNet Option
Mobile users with a NATEL® go subscription can be integrated into the beemNet ecosystem through the activation of a user license. Once linked to a user identity, traffic is secured through the beem app, ensuring encrypted, policy-compliant communication across any network (e.g., WLAN, mobile).
Integration with Swisscom Mobile Network via Protect & Connect User Licenses
Users without a business mobile subscription can be onboarded with a Protect & Connect license. This grants them access to the beemNet services on up to one device and includes the use of the beem app. The Protect & Connect license ensures traffic is routed through the Swisscom security layer, applying all security levels and inspections.
Endpoint IP Address Cloaking
The "Endpoint IP Address Cloaking" feature ensures that the IP addresses of client devices and sites secured with beem are hidden. This is achieved through the use of "Carrier-Grade Network Address Translation (CGNAT)," a technique that utilizes the shared address space specified in RFC 6598, which is intended for service provider networks like Swisscom's. By employing CGNAT, beem treat the customers’ IP addresses as private, keeping them concealed from the public internet. Consequently, website owners and similar entities only see a generic public IP address from a shared pool of public IP addresses, ensuring that the actual IP addresses of beem visitors remain hidden and secure. This prevents websites from seeing and tracking individual device IP addresses. Hence, privacy and security are enhanced, providing better protection against targeted attacks like Denial-of-Service (DoS) and Social Engineering.
Masking the Source (User) Identity
To preserve user privacy and protect endpoints from targeted attacks, the public IP address of user devices is obfuscated when accessing the internet. This ensures that the actual source address is not visible to external entities, reducing traceability and attack surface. Even with cloaking enabled, we always ensure that the shared public IP address presented to the internet is Swiss.
Unified Threat Management
E-Mail Security for SMTP, IMAP, MAPI, POP3
Email security is delivered via a proxy that inspects mail protocols such as SMTP, IMAP, POP3, and MAPI. The inspection includes:
- Signature-based malware detection
- Spam and phishing filtering
- Content and attachment scanning
- Blocking of malicious senders and domains
Fixed IPs are required for server-to-server communication. This feature is available starting with the Premium Security Edition and complements broader Data Loss Prevention (DLP) strategies.
Outbound Traffic
Internet Access via beemNet
All outbound internet traffic is routed through the beemNet infrastructure, applying policy enforcement at the DNS, IP, and application level. Users benefit from URL filtering, Deep Packet Inspection (DPI), TLS/SSL decryption, and threat reputation services. Swisscom may apply bandwidth throttling per device or site to ensure consistent protection levels across its shared infrastructure.
WARNING
Services that require public-facing IPs (e.g., dynDNS) are not compatible with beemNet due to IP cloaking.
