Secure Access to Business Applications
Secure Access Anywhere with Zero Trust and the beem app
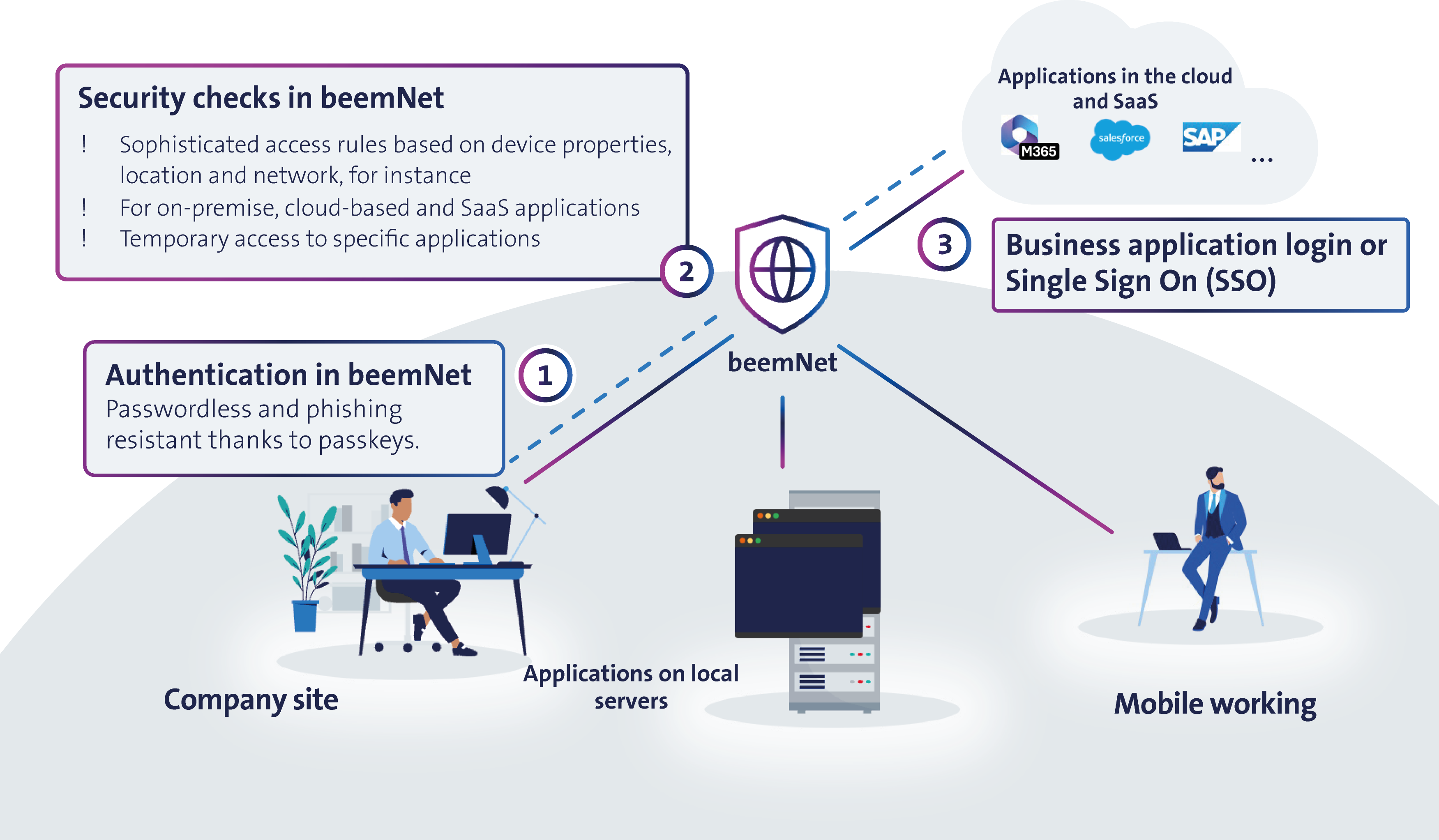
The Standard, Plus, and Premium Security Editions offer robust features designed to safeguard access to business applications and sensitive company data. At the heart of these Security Editions is a Zero Trust access model, which ensures that access is never granted by default—it is always verified based on dynamic, context-specific conditions.
With Zero Trust, access depends on real-time context such as:
- User identity
- Network
- Device properties, security, and identity
- Data sensitivity
- Location
- Time of access
- Whether the device is up to date
- And more
This means a user might be able to access a business application one day, but not the next—perhaps because they’re in a different country or the device is missing a required update. In short, access is smart, adaptive, and temporary, reducing risk by limiting it to specific applications rather than the entire network. The beem app allows users to securely access business apps from anywhere and any device. Whether hosted in the cloud, on internal company servers, or as SaaS applications like Microsoft 365, Salesforce, or Workday, Zero Trust ensures that only authorized users can gain access.
INFO
The beemNet also incorporates various technologies to ensure secure access without relying on the beem app, such as Remote Browser Isolation, the Business Application Portal, among others.
All business applications—on-premises, cloud, or SaaS—are securely connected to the beemNet, a centralized and secure access point. Uniform and granular access rules ensure consistent protection. No matter where users are working from, all access is routed through the protected beemNet. Access is also temporary and limited to specific applications, not the entire network. This prevents attackers from moving laterally within the system.
Secure Access with beem: How It Works
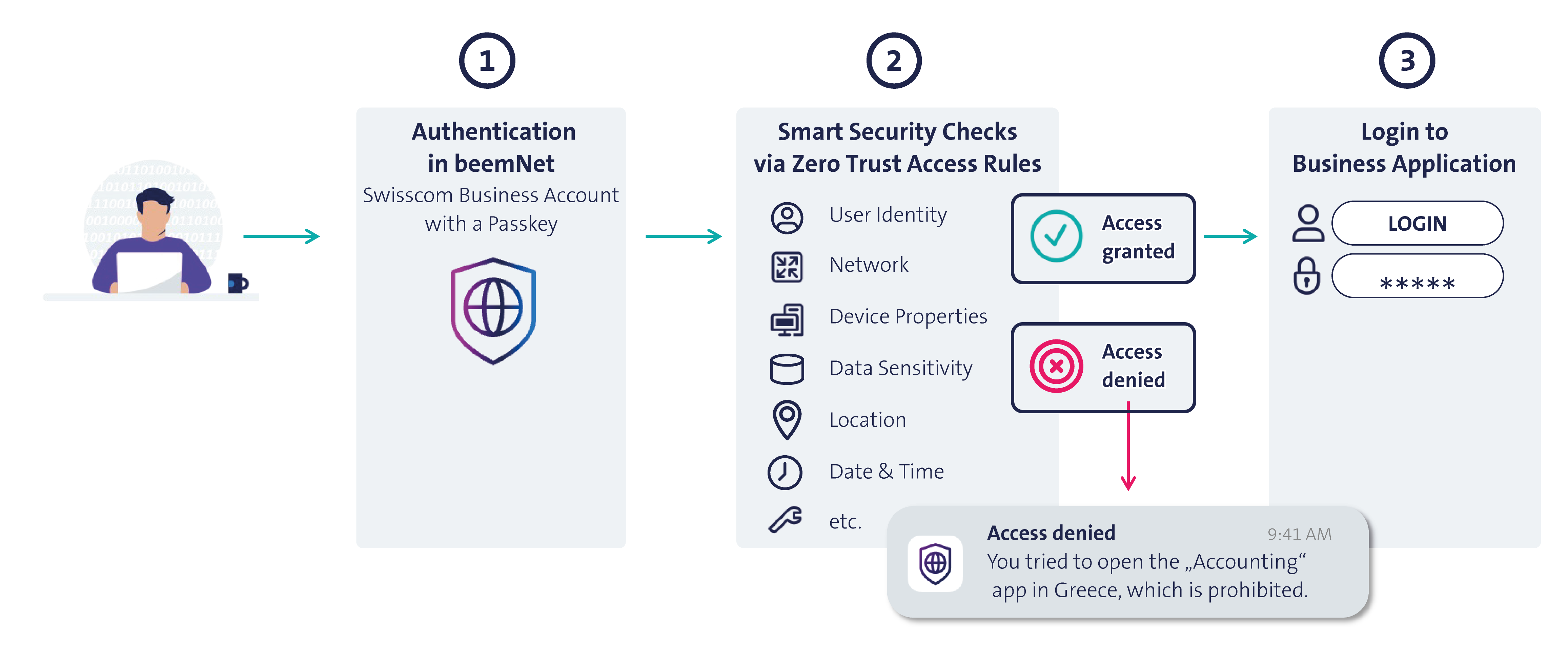
① Strong, Phishing-resistant Authentication in beemNet Before logging into any business application, users must first authenticate through beemNet. By default, this is done using Passkeys—a modern and secure authentication method that leverages fingerprint, facial recognition, or a PIN. Passkeys adhere to the highest security standards and are inherently resistant to phishing attacks.
② Smart Security Checks by applying Zero Trust Access Rules Access is governed by fine-grained, context-aware Zero-Trust policies defined by the beem administrator. Because beem continuously enforces these security checks in real time, a user may lose access even during an active session—for example, if their device becomes non-compliant due to a missing update, a disabled screen lock, or other posture violations.

Temporary access to a business application is granted only if all checks succeed.
If any check fails, the user receives an instant push notification, and access is denied.
③ Legacy Login to Business Applications Once authenticated through beemNet, users can log in to their business applications using their existing accounts as usual. If the company uses Swisscom Business Accounts with identity federation, this step can even be skipped entirely, resulting in a seamless and streamlined experience.
